May 2022 | Cyber Threats
May 12, 2022
Cyber Awareness: Common Scams and Email Threats May 2022
There has been an upsurge of scamming and phishing threats, particularly in financially oriented service companies. We urge all clients to be vigilant when opening mail from unknown senders that contain links.
The closer an attacker comes to stealing credentials, the harder they will target that user going forward.

1. Pop-Up Window Alerts
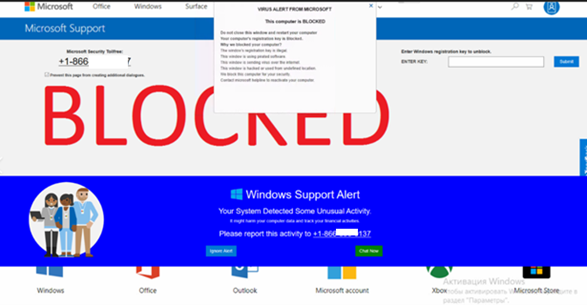
This specific scam is referred to as “This computer is blocked” Virus Alert.
It is used to trick users into paying for support. They use the impression that they are Microsoft support team members. Note that Microsoft has nothing to do with this. Scammers attempt to give the impression that there is a problem with the system (the computer is infected, damaged, and so on) and trick people into contacting them via telephone numbers. Once connected, bad actors can install software, keyloggers, transfer data, or access your auto-saved passwords to work from Amazon, bank accounts, web email accounts, and more.
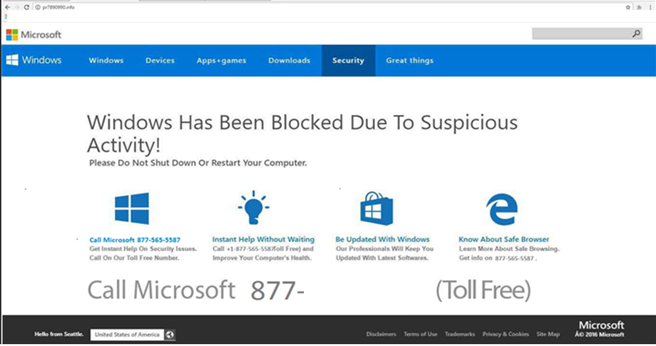
To avoid this and remove this window simply close the opened window and never return to the site. If the website prevents you from closing it, close the entire browser or terminate the browser process using Task Manager. Do not restore the closed session the next time you open your browser – this will lead you to a deceptive website (or the website that led you to this dubious site in the first place).
2. Email Phishing With Fake URL Login Portal
Email phishing is a common practice for bad actors trying to trick users into manually entering personal information leading to a malicious website. Despite how skilled bad actors have become at the psychological manipulation component of phishing, there are still tell-tale signs you can look for to avoid clicking through a phishing message.
Have a level of distrust and don’t blindly click a link to log into important accounts without verifying the URL is correct. A popular tactic is asking users to “verify your account,” so you click through a link and enter your username and password, delivering the goods right to the wrong people.
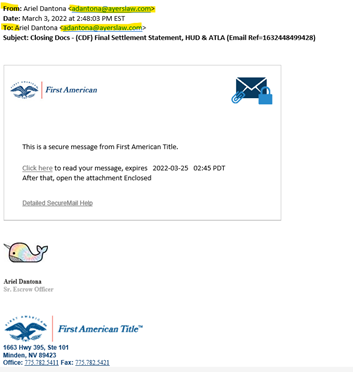
The fake portal will never authenticate and simply will process and store all log-on attempts. As you try your known passwords, you are actively giving away SENSITIVE information to the bad actors who then aggregate all this data in chats and forums on the DARK WEB with the intent of compiling a list of known good passwords and possible logons.
What Can You Do To Protect Your IT Infrastructure?
Utilize Office365 Spam Filtering & Rules
- Block Known malicious IP's and Domains
- Create a [WARNING] Tip for external mail
- Train users on phishing scams
- Enforce MFA on all accounts
Recent News
Looking for Help?
Interested in learning more about IT support or cybersecurity options?
- 70 Charles Lindbergh Blvd, Suite 4. Uniondale, New York 11553
- (+1) 844-WEKNOW1
- info@securendsolution.com
















